A brand-new danger in the always changing field of cybersecurity is known as the "Terrapin attack." This advanced vulnerability exploits a flaw in the SSH (Secure Shell) protocol, which is essential for safe computer-to-computer communication. Let's investigate this attack in more detail so that we may better grasp its complexities, possible outcomes, and defenses.
Demystifying the Terrapin Attack
The Terrapin attack, denoted by the CVE-2023-48795 classification, is a novel security flaw in the SSH protocol. SSH is at the core of this new threat since it is essential for secure server access and for functions like file transfers and remote logins.
The Inner Workings of the Terrapin Attack
The Terrapin assault is based on a new method known as prefix truncation. A hostile actor can tamper with the vital SSH handshake procedure using this technique. Through the intentional injection of random SSH messages during the key exchange and the subsequent removal of an equal number of messages, the attacker is able to undermine the security of the connection that has been created.
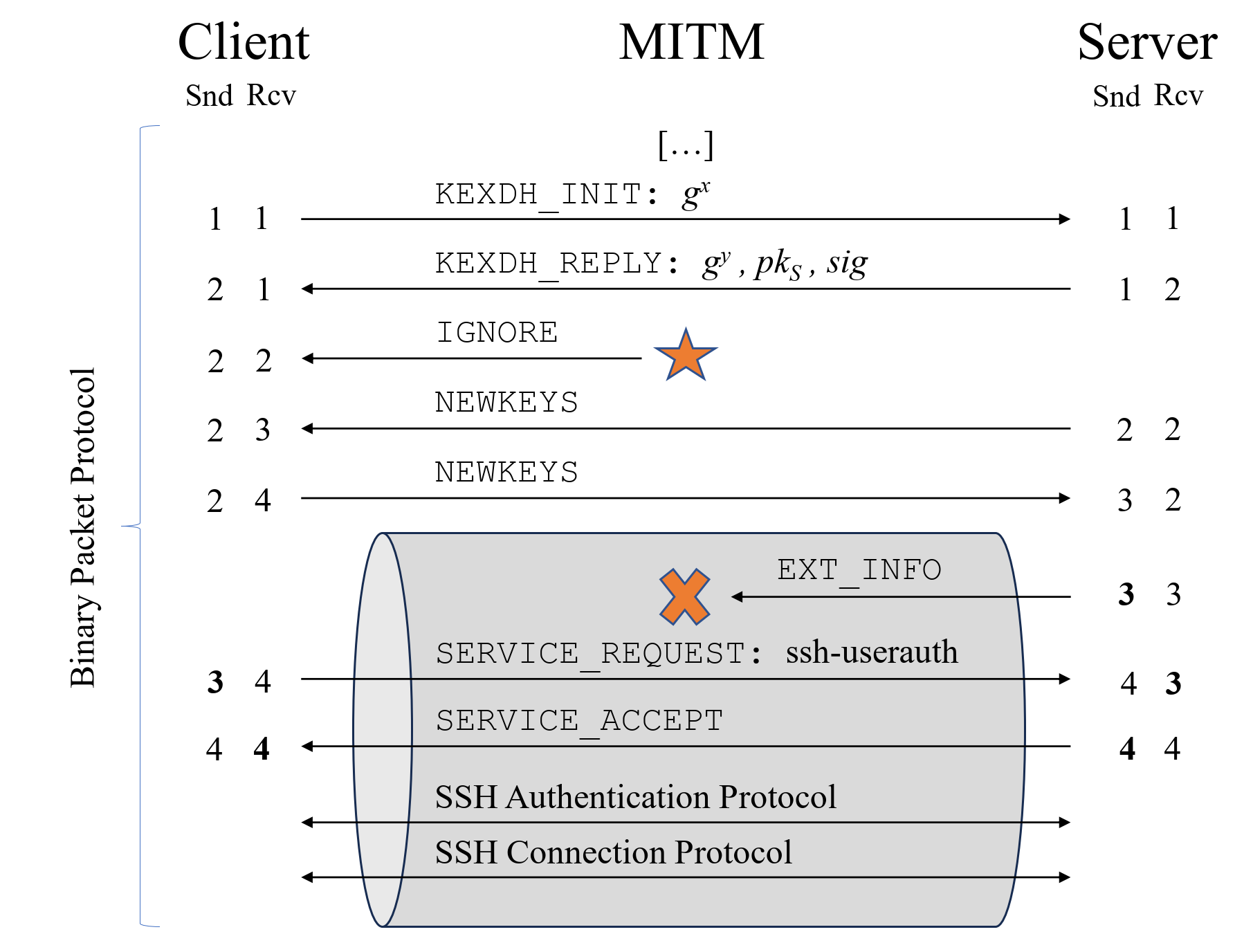
The above image demonstrates how the Terrapin attack is used in real life. Without the client or server realizing, the attacker can drop the EXT_INFO message, which is needed to negotiate multiple protocol extensions. Sequence numbers would typically mismatch, allowing the client to notice packet deletion when it received the subsequent binary packet from the server. An attacker injects a packet that is ignored during the handshake to offset the sequence numbers appropriately in order to prevent this.
The attack relies on taking advantage of flaws in certain algorithms that SSH uses; ChaCha20-Poly1305 and Encrypt-then-MAC are the two main targets. These methods, which are commonly used in SSH implementations, can be downgraded, which could put the connection at serious danger of security breaches.
The Ripple Effect: Impacts of the Terrapin Attack
The Terrapin attack casts a wide net of consequences, impacting SSH connections in multiple dimensions:
Connection Security Downgrade: The attack can actively downgrade the security posture of SSH connections, rendering them vulnerable to exploitation.
Algorithm Compromises: Focusing its assault on algorithms like ChaCha20-Poly1305 and Encrypt-then-MAC, the attack compromises the integrity of these widely adopted cryptographic methods.
Countermeasure Disabling: In certain versions of OpenSSH, the Terrapin attack has the potential to disable countermeasures designed to protect against specific security threats.
Man-in-the-Middle Exploitation: Beyond connection downgrades, the attack opens avenues for Man-in-the-Middle (MitM) scenarios. This creates opportunities for attackers to exploit implementation flaws and gain unauthorized access.
Fortifying Against the Terrapin Attack
Mitigating the Terrapin attack requires a strategic approach:
Strict Key Exchange: Consider adopting a "strict kex" protocol in SSH handshakes. This modification acts as a safeguard, preventing the introduction of unauthenticated messages and sequence number manipulation by potential Man-in-the-Middle attackers.
- Note: For effectiveness, both the client and server must support this countermeasure.
Temporary Algorithm Disablement: As a stopgap solution, contemplate temporarily disabling affected algorithms such as ChaCha20-Poly1305 and leveraging alternatives like AES-GCM until patches are readily available.
Actionable Steps for Developers and Administrators
For those actively involved in the development and management of SSH implementations, proactive steps are paramount:
Update Software: Ensure your SSH implementations, including OpenSSH and AsyncSSH, are up-to-date with the latest patches addressing the Terrapin vulnerability.
Implement Countermeasures: Embrace recommended countermeasures like the "strict kex" protocol to fortify the security of your SSH connections.
Stay Informed: Regularly monitor security updates and advisories from your SSH implementation providers. Subscribe to relevant security mailing lists for timely notifications.
User Education: If you manage SSH servers, educate users about the criticality of updating their SSH clients and adhering to secure practices.
Mitigation Steps for Red Hat Enterprise Linux Users
If you are a user of Red Hat Enterprise Linux 7, 8, or 9, Red Hat provides detailed mitigation steps on their official page. You can visit Red Hat's CVE-2023-48795 page to apply the necessary patches or follow their recommended steps to enhance the security of your SSH connections. Stay informed and secure your systems against potential vulnerabilities.
In Conclusion
Comprehending and countering dangers such as the Terrapin attack is essential in the ever-changing realm of cybersecurity. With the right information, patching requirements met, and countermeasures put in place, users and developers may strengthen their SSH connections against potential threats. A strong and resilient computing environment continues to be built on proactive security measures.
For in-depth information and updates on the Terrapin attack, consult the official Terrapin Attack website.
Stay secure, code responsibly!