Introduction
Software security has become a top priority in a world that is becoming more and more digital. Constantly on the search for weaknesses to exploit, hackers and other bad actors. Buffer overflows are a frequent attack method that, if left unchecked, can have disastrous effects. The Stack-Smashing Protector (SSP), one of the effective tools and methods to counter these attacks, is fortunately available. We'll go into the world of SSP in this blog article, looking at its goals, how it's put into practice, and the crucial part it plays in protecting software against exploitation.
Understanding Buffer Overflows
Let's first understand the concept of buffer overflows before delving into SSP. When a program writes more data into a buffer (temporary storage region) than it can hold, a buffer overflow occurs. This extra data has the potential to overwrite nearby memory, resulting in unpredictable and frequently dangerous behavior. Hackers use buffer overflows to run arbitrary code, take control of a machine, or crash software.
The Stack and Its Vulnerabilities
We must examine the call stack, a vital element of program execution, in order to understand SSP's function. A program keeps return addresses, local variables, and information about function calls on a section of memory called the stack. According to the "Last-In-First-Out" (LIFO) concept, the function that has been called the most recently is at the top of the stack.
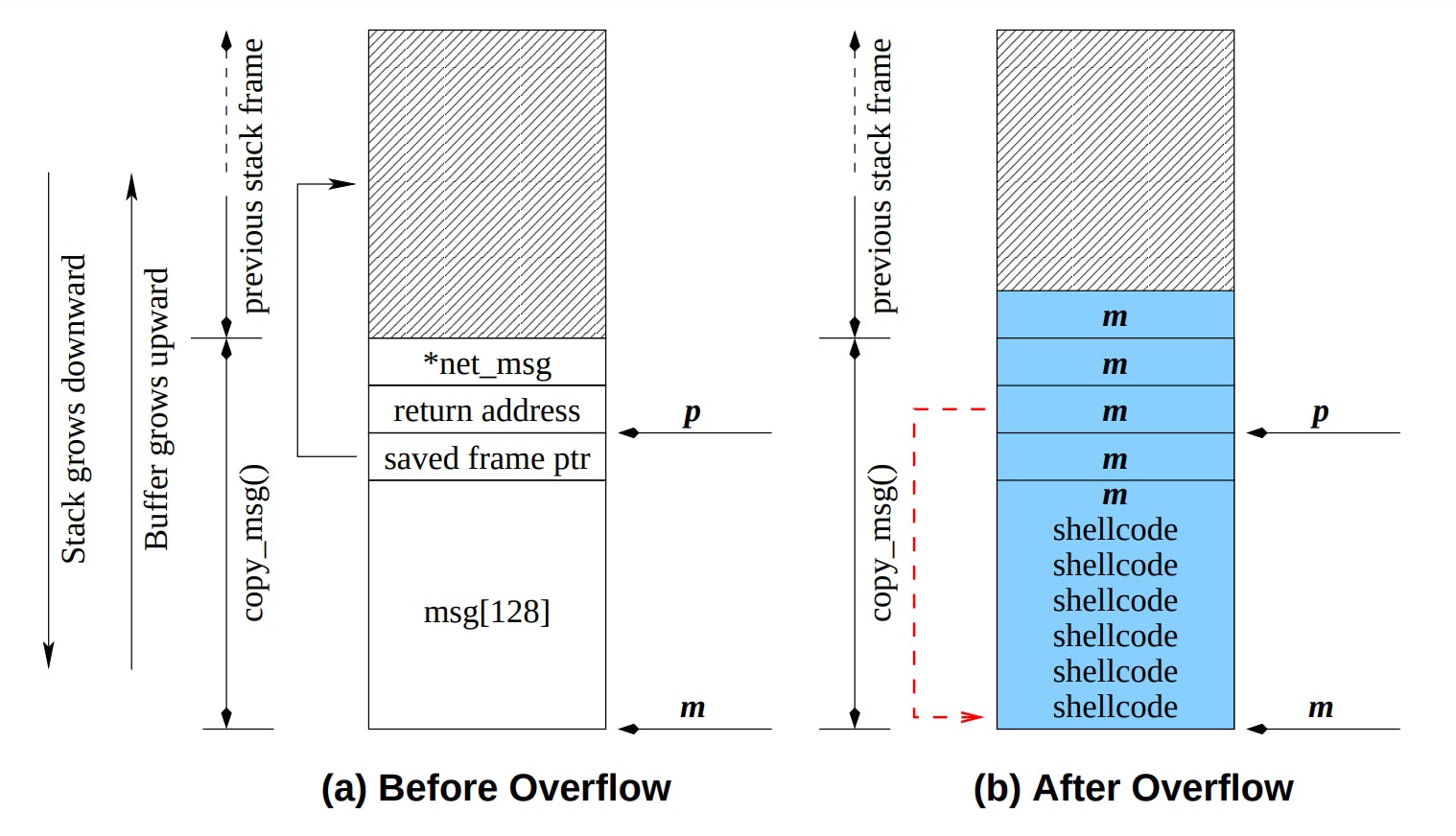
When a program writes extra data into a buffer that is located on the stack, stack-based buffer overflows happen. The layout of the stack is well-defined and predictable, so attackers can focus on particular memory addresses to run malicious code or alter program logic. For many years, hackers have favoured this weakness.
Enter the Stack-Smashing Protector (SSP)
Think of the stack as a collection of plates, each plate standing in for a function call or a data frame. The stack canary resembles a secret plate sandwiched in between the visible plates. Its purpose is to identify any tampering attempts with the stack.
Here's how it functions:
Initialization: The stack canary, a random or semi-random value, is created upon program launch.
Placement: In the stack frame of a function, this canary is positioned between the local variables and the saved return address.
Protecting the Nest: The canary should remain unchanged as the function runs. The canary is probably going to get overwritten if there is a buffer overflow or stack corruption.
Detection: Before the function exits, SSP checks to see if the stack canary has changed. If it has, an overflow of the stack buffer has occurred.
Response: In the event that a breach is discovered, SSP may start or stop the program, send out a security notice, or activate additional security measures.
SSP in Action
Let's go over a straightforward example to see how SSP functions. Think about a C program that has a weak function:
#include <stdio.h>
#include <string.h>
void vulnerable_function(char *input) {
char buffer[64];
// Vulnerable code that doesn't check buffer size
strcpy(buffer, input);
}
int main(int argc, char *argv[]) {
if (argc != 2) {
printf("Usage: %s <input>\n", argv[0]);
return 1;
}
vulnerable_function(argv[1]);
printf("Program executed successfully!\n");
return 0;
}
The vulnerable_function in this code, copies command-line input into a buffer without determining its size. This flaw could be used by an attacker to launch a stack buffer overflow attack. The stack canary will be inserted, and the integrity of the stack will be monitored, if SSP is enabled during compilation. In the event of an overflow, SSP will recognize it and stop any malicious execution. For the GCC (GNU Compiler Collection) and Clang compilers, you can enable SSP using the -fstack-protector flag. There are different levels of SSP that you can choose from, including all, strong, and none. The default level is usually strong. Here's how you can enable SSP:
gcc -o test test.c -fstack-protector
Advantages of SSP
Stack-Smashing Protector offers the following major advantages:
Enhanced Security: A strong defense against stack-based buffer overflow attacks, a popular attack method for hackers, is provided by SSP. It assists in preventing unwanted access and code execution by spotting stack manipulation.
Automatic Protection: SSP operates automatically once it is turned on during compilation. For each function or codebase, developers do not need to manually install unique security measures.
Widespread Support: SSP is supported by a large number of contemporary compilers and operating systems, making it available for a variety of programming languages and applications.
Cost-Effective: Since SSP doesn't require major alterations to current codebases, it is a cost-effective security strategy. With little effort, it adds an additional layer of security.
Continuous Improvement: SSP and comparable security measures have developed over time to handle new threats and vulnerabilities, enhancing their effectiveness.
Considerations and Limitations
SSP is a useful security feature, but it's important to understand its limitations:
Not a panacea: SSP is not a comprehensive remedy for all security flaws. It may not offer protection from other forms of attacks, like heap overflows or logic problems, as it exclusively targets stack buffer overflows.
False Positives: SSP occasionally produces false positives that force program shutdown even if no genuine attack is taking place. To counteract this, proper testing and debugging are crucial.
Platform and Compiler Dependency: Depending on the compiler and platform being used, SSP's accessibility and behavior may change. Developers should confirm settings and compatibility with their particular environment.
User education: It's crucial that developers comprehend how SSP functions and why it's crucial to enable it. Systems can become vulnerable due to incorrect configuration or omitting to activate SSP.
Final Thoughts: The Fight for Software Security
Software security continues to be a constant battle in a landscape of cyber threats that is constantly changing. SSP, a fundamental protection mechanism, is essential for reducing the dangers posed by stack buffer overflows. It is only one part of the puzzle, though. Software must be protected against increasingly complex threats by combining SSP with a comprehensive security strategy that includes testing, awareness, coding standards, and close monitoring.
The software development community must continue to be dedicated to strengthening security precautions, adjusting to new threats, and remaining one step ahead of those who attempt to exploit vulnerabilities for nefarious purposes as technology develops and new vulnerabilities appear. In the ongoing endeavor to develop more secure software ecosystems, SSP is a useful tool.